The guide below details how to setup a single sign-on integration in the LogiSense Billing application. Both Azure AD and Okta integrations are covered in this guide.
Okta Configuration Process
Setup a new Application in the Okta Admin Portal
The fist step is to create an application in the Okta portal for the LogiSense Billing integration.
On the left hand side click on Applications to show the sub menus
On the Applications sub menu click Create App Integration
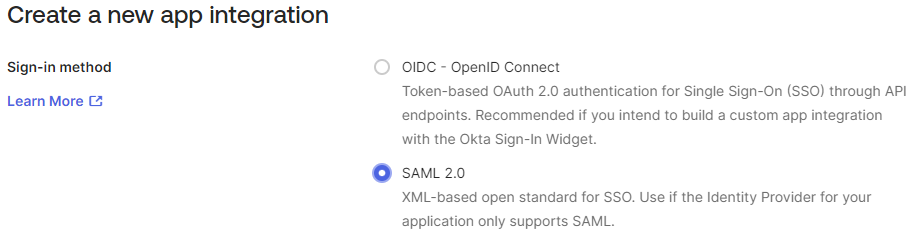
On the Create New App Integration pop-up select SAML 2.0 and click Next
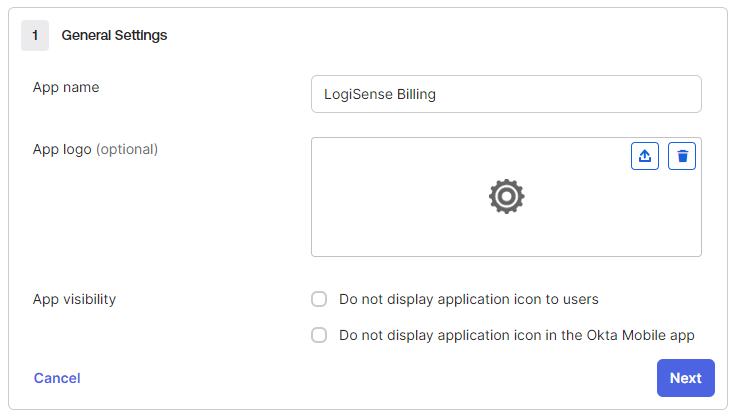
On the Create SAML Integration page enter an application name (for instance, LogiSense Billing) and click Next
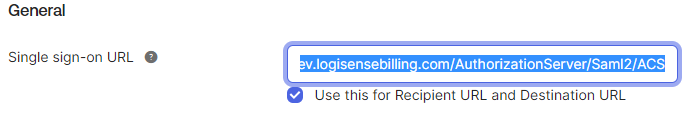
Enter the Single sign-on URL. This will be the URL used to access your LogiSense Billing instance plus the path to the AuthorizationServer ( /AuthorizationServer/Saml2/ACS )
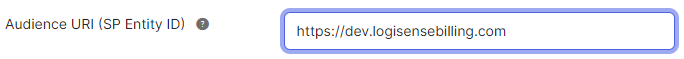
Enter the Audience URI (this will be the same domain name as above, but without the AuthorizationServer… details)
All other settings can be left as default, at the bottom of the page click Next
On the following page select I'm an Okta customer adding an internal app option and then the This is an internal app that we have created option and click Finish
Capture SAML Certificate Details
Next certain details are required from the Okta application data in order to configure SAML settings in the LogiSense Billing application. You can copy these details into notepad or any text editor.
On the application page that loads scroll down to the SAML Signing Certificates section
Next to the SHA-2 cert click on Actions and then View IdP metadata
On the metadata page that loads copy the url of that page (e.g. https://dev-xxxxxxxx.okta.com/app/exkaffbk7gT0TrGxi8d7/sso/saml/metadata) and copy the value within that page on the very first line called entityID
Configure the SAML Settings in LogiSense Billing
Login to LogiSense Billing
Load the Setup / Users & Accounts / Owners screen
Under Owner Configuration click on SAML Setting
Click Enabled if it is not already selected
In the Entity ID field paste in the entity id from the metadata (just the URL without quotes)
In the Provider Metadata URL field paste in the metadata URL you previously copied
Click the Get Token button and a token will be generated
Copy the SCIM Access Token that is generated (this will be needed as part of the SCIM Configuration below)
Click Save to save the SAML settings
Configure SCIM to Manage Users
Access the Okta admin portal
Access the Application you setup for the LogiSense Billing integration
Click on the General link
Under the App Settings section click Edit
Check the option Enable SCIM provisioning
Click Save
Once the change is saved a new Provisioning link will appear under the application where SCIM settings can be populated
Click on Provisioning
On the Provisioning Settings page click Edit
In the SCIM connector base URL field enter the domain of your LogiSense Billing system followed by /ResourceServer/api/SCIM
In the Unique identifier field for users field enter your Okta supplied identifier
In the Supported provisioning actions section enable Push New Users, Push Profile Updates and Push Groups
Change the Authentication Mode to HTTP Header authentication
Under the HTTP Header section in the Bearer field paste the SCIM Access Token you copied earlier from the SAML Settings in the LogiSense Billing application
Click Test Connector Configuration
On the pop-up that appears the test should show that the testing of the create, update and push functions worked
==
Test config failure, need to sort this out (note SCIM settings cannot be saved because of this)
More steps to add here
==
Test the SAML Integration
Log out of LogiSense Billing
On the Login page a new Log in with SSO option will be available